300 Indian Banks Become Disabled by a Massive Ransomware Attack, Severely Affects ATM and UPI Services
300 Indian Banks Become Disabled by a Massive Ransomware Attack, Severely Affects ATM and UPI Services
Regulatory bodies responded promptly to the attack. The National Payment Corporation of India (NPCI) temporarily restricted C-Edge Technologies‘ access to its retail payment network in order to prevent the potential dissemination of the cyber threat.
According to officials, although nearly 300 banks have been cut off from the network, these institutions represent a minor segment of about 0.5% of the nation’s total payment system volumes.
A significant ransomware attack has caused the operations of approximately 300 local banks in India to be disrupted.
The majority of the affected institutions are rural and cooperative establishments. C-Edge Technologies, a main provider of financial solutions for these smaller firms, was the target of this cyberattack, which took place on Wednesday. As a result, severe payment system failures were caused, as reported by Reuters.
The regulatory agencies moved quickly in response to the incident that had just occurred. In order to prevent the cyber threat from spreading further, the National Payment Corporation of India (NPCI) took the precautionary measure of temporarily cutting off C-Edge Technologies’ access to its retail payment network.
Customers who were customers of the affected banks discovered that they were unable to use a variety of payment services as a consequence.
There are around 1,500 cooperative and regional banks in India’s banking system, the majority of which service regions that are located outside of the country’s major cities.
As a result of the attack, a considerable chunk of this industry has been significantly impacted, which has raised serious concerns over the cybersecurity protections that are in place for rural banking infrastructure.
Comprehensive audits are currently being carried out by regulatory agencies in order to assess the damage and prevent any additional problems from occurring. On the other hand, the Reserve Bank of India (RBI) has not yet publicly published any pronouncements regarding the current situation.
During this period of isolation, the banks that were impacted by the disconnection will experience disruptions in their payment systems, according to an alert issued by the National Payments Corporation of India (NPCI). This measure is being taken with the intention of protecting the payment infrastructure of the country as a whole.
Executive Summary
The threat research team at CloudSEK is keeping a close eye on a big ransomware attack that has caused disruptions in India’s banking environment, affecting both banks and payment providers. The purpose of this research is to analyze the attack chain, identify the strategies employed by adversaries, and provide companies with insights that can be put into action to improve their security posture. This study will include continual updates and recommendations to handle the ever-changing threat scenario. This is because the issue is still unfolding.
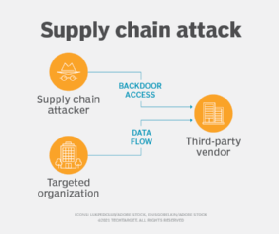
In this particular instance, Brontoo Technology Solutions, which is a significant collaborator with C-EDGE, a joint venture between TCS and SBI, is the firm that is most affected. The purpose of this report is to investigate the more far-reaching effects that this attack has on the environment.
Understanding the Potential Attack Chain
According to the report that was submitted by Brontoo Technology Solutions with CERT-In (Indian Computer Emergency Response Team), it was indicated that the attack chain began at a Jenkins server that had been misconfigured. Additionally, the CloudSEK threat research team was successful in determining the Jenkins server that was compromised and, as a result, the attack chain.
Within the past few years, we have published a substantial amount of material concerning the exploitation of Jenkins by means of a local file inclusion vulnerability. You can read about the case study here, and you can read about the entire exploit chain here.
- Vulnerability: CVE-2024-23897: Because the Jenkins instance that Brontoo Technology uses was vulnerable to the same LFI CVE, it is possible to use it to read internal code or, in this particular instance, to gain secure shell access by reading the private keys. Both of these options are possible because port 22 was open.
- One of the most important aspects of the ransomware industry is the Initial Access Brokerage. Based on the history and current attack chains that have been exploited, we have a low level of confidence in our suspicion that this access may have been sold by IntelBroker, a threat actor and moderator from breach forums, to the RansomEXX group for the purpose of further exploitation.
Analysis and Attribution
We have reached the conclusion that RansomEXX is the ransomware group that is responsible for this attack. This conclusion was reached by our study and the utilization of sensitive sources. The substantial engagement that we had with the banking sector in India that was impacted made this judgment much easier to arrive at.
The RansomEXX v2.0 ransomware is a sophisticated form of the RansomEXX malware, which is notorious for focusing on major enterprises and demanding substantial ransom payments. This organization is part of a larger trend in which ransomware writers are constantly evolving their software in order to circumvent security measures and increase the impact of their attacks.
For more info, you can visit the CloudSec official page possessing the desired details.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
READ MORE ARTICLE HERE










