The ONNX Phishing Service is Designed to Target Microsoft 365 Accounts at Financial Institutions

The ONNX Phishing Service is Designed to Target Microsoft 365 Accounts at Financial Institutions
Through the use of QR codes embedded in PDF files, a new phishing-as-a-service (PhaaS) platform known as ONNX Store is attempting to compromise Microsoft 365 accounts belonging to personnel working for financial institutions.

Two-factor authentication (2FA) bypass mechanisms are included in the platform, which can target email accounts associated with Microsoft 365 as well as Office 365. Additionally, the platform communicates through Telegram bots.
ONNX is believed to be a renamed version of the Caffeine phishing kit, which is handled by the Arabic-speaking threat actor MRxC0DER, according to the researchers at EclecticIQ who identified the activity.
In October of 2022, Mandiant made the discovery of caffeine. At the time, the platform was exclusively targeting Russian and Chinese platforms rather than Western services.
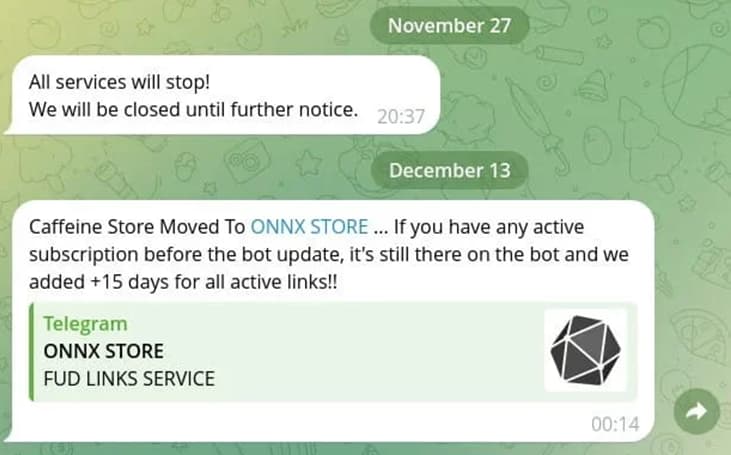
Announcement of rebranding
Source: EclecticIQ
ONNX Attacks
In February of 2024, EclecticIQ spotted assaults carried out by ONNX. These attacks consisted of the distribution of phishing emails with PDF attachments that contained harmful QR codes. These emails were directed at personnel working for banks, credit union service providers, and private funding organizations.
In the emails, human resources (HR) departments are impersonated, and updated pay information is used as a lure to open the PDFs, which are designed to look like they were created by Adobe or Microsoft.
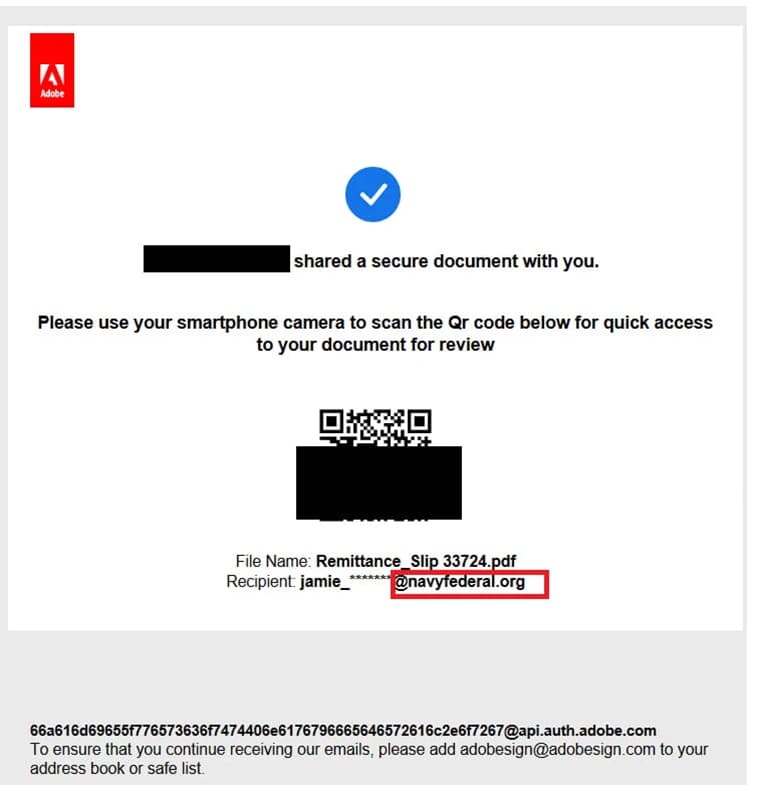
Malicious PDF attachment
Source: EclecticIQ
After scanning the QR code on a mobile device, users are taken to phishing pages that resemble the real Microsoft 365 login interface. This allows the phishing attacks to evade the defenses that are in place on the companies that are being targeted.
The Microsoft 365 phishing page
Source: EclecticIQ
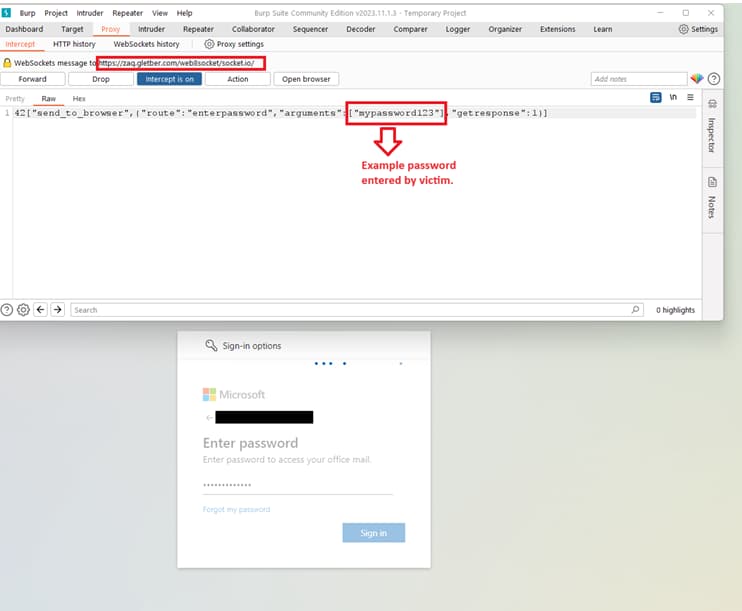
When the victim visits the false login page, they are invited to enter their login credentials and two-factor authentication token. The phishing website then records these details in real-time after they are entered.
WebSockets are used to immediately transmit the stolen credentials and two-factor authentication tokens to the attackers. This gives the attackers the ability to take control of the target’s account before the authentication and multi-factor authentication tokens expire.
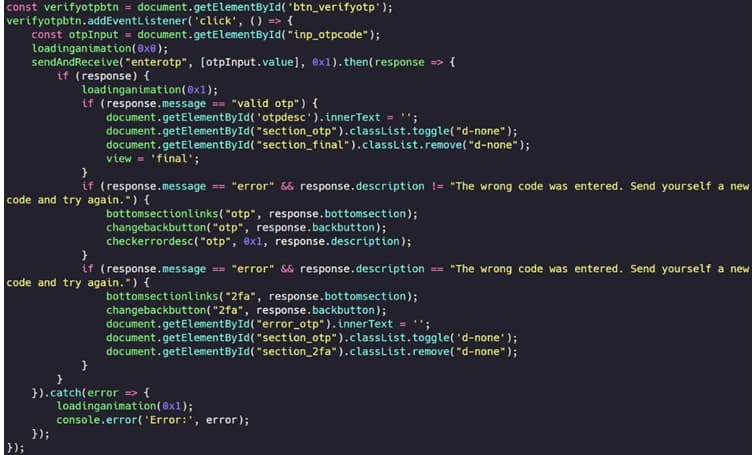
The 2FA bypassing mechanism
Source: EclecticIQ
Because of this, the attackers are able to gain access to the hacked email account, which allows them to steal important information such as emails and documents. Additionally, they can sell the credentials on the dark web in order to launch ransomware and malware assaults.
Highly Effective Phishing Platform
When viewed from the point of view of cybercriminals who make use of the service, ONNX has the potential to be an attractive and economical platform. Clients are able to manage their phishing activities through an easy-to-use interface thanks to bots that are located on Telegram, which serves as the operational hub. In addition, there are help channels that are specifically designed to assist consumers with any problems they may be experiencing.
For the purpose of sending phishing emails to targets, webmail services are accessible, and the phishing templates that come with Microsoft Office 365 can be customized. An additional degree of obfuscation is added by the ONNX phishing kit, which makes use of encrypted JavaScript code that decrypts itself during page load. This provides an additional layer of protection against detection by anti-phishing programs and scanners.

In addition, ONNX makes use of Cloudflare services, such as an anti-bot CAPTCHA and IP proxying, in order to prevent its domains from being taken down.
Moreover, there is a bulletproof hosting service that guarantees that the operations will not be disrupted by reports and takedowns. Additionally, there are remote desktop protocol (RDP) services that have been implemented to ensure the secure management of the campaigns.
All in all, customers who have Microsoft 365 accounts are particularly vulnerable to the dangers posed by the ONNX Store, particularly businesses that are involved in the wider financial services industry.
It is suggested that administrators ban PDF and HTML attachments from unverified sources, limit access to HTTPS websites with untrusted or expired certificates, and set up FIDO2 hardware security keys for high-risk, privileged accounts in order to defend themselves against the sophisticated phishing attempts that are being launched by this threat.
YARA rules have also been included in the report that EclecticIQ has distributed in order to assist in the detection of malicious PDF files that contain QR codes that lead to phishing URLs.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE