Packet Manipulation With Scapy

Packet Manipulation With Scapy
Scapy is written in Python by Philippe Biondi. It is used for packet manipulation With Scapy in networks. Scapy can forge or decode packets, send them on the wire, catch them, and match requests and replies. It can likewise deal with errands like scanning, tracerouting, probing, unit tests, attacks, and network discovery.
Features of Scapy:
- Packet Manipulation
- Packet Capture
- Match Requests and Replies
- Scanning
- Tracerouting
- Probing
- Attacks
- Network Discovery
How to install Scapy?
Step 1: Clone the repository
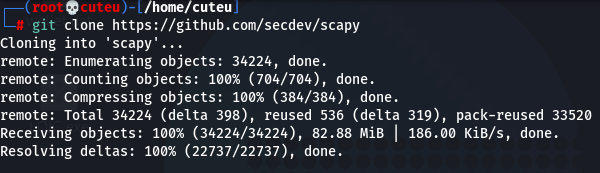
git clone https://github.com/secdev/scapy
Step 2: Change the directory
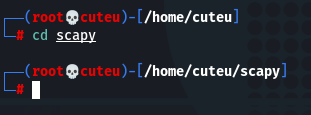
cd scapy/
Step 3: Run the “run_scapy”
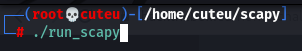
./run_scapy
How to install Scapy with pip?
pip install scapy
How to packet manipulation with Scapy?
Send Packet
send(): Send packets at Layer 3
IP(): Define Source IP and Destination IP
ICMP(): Internet Control Message Protocol
src: Source IP
dst: Destination IP
Syntax
send(IP(src=”Source IP”,dst=”Destination IP”)/ICMP()/”Text”)
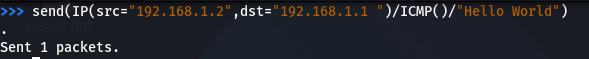
Example:
send(IP(src=”192.168.1.2″,dst=”192.168.1.1 “)/ICMP()/”Hello World”)
Check response in Wireshark:
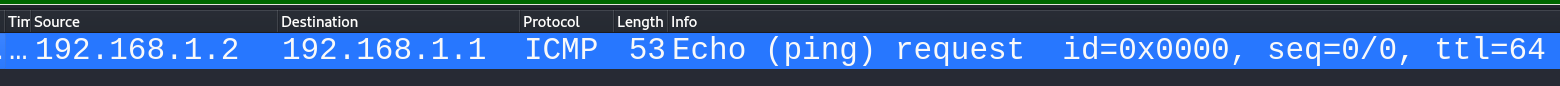
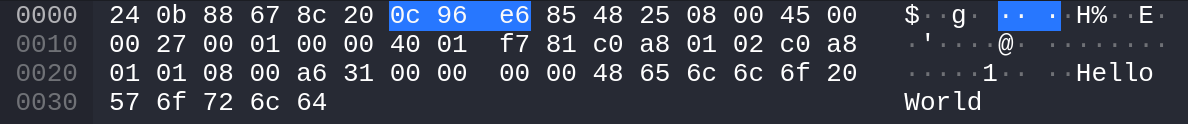
Sniff Packet
Iface: Name of interface
prn: function to apply to each packet
lambda: we can now perform custom actions with each sniffed packet.
X: variable
x.summary: Print the summary of the output
Syntax
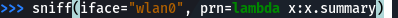
sniff(iface=”Interface”, prn=lambda x:x.summary)
Example
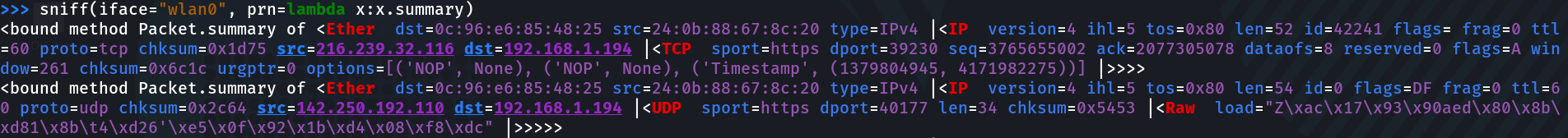
sniff(iface=”wlan0″, prn=lambda x:x.summary)
Output:
Send multiple packet
TCP: Transmission Control Protocol
sport: Source port
dport: Destination port
count: number of packets
Syntax
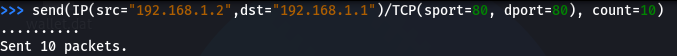
send(IP(src=”Source IP”,dst=”Destination IP”)/TCP(sport=Source port, dport=Destination port), count=number of packets)
Example
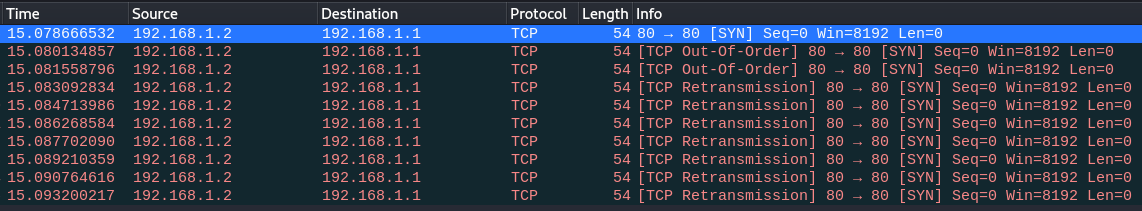
send(IP(src=”192.168.1.2″,dst=”192.168.1.1″)/TCP(sport=80, dport=80), count=10)
Check response in Wireshark:
Home: – https://scapy.net/
You May Also Like To Read
How to protect yourself from hackers 2021
Joint Cyber program UK | US and Australia Press Release
Nuclei Vulnerability Scanner tools | fast and customizable








