Candiru’s Spyware Project Proposal Leaked

Candiru’s Spyware Project Proposal Leaked
Israel is one of those countries whose business houses and governments invest a lot in human capital to provide hackers. Candiru Spyware is one of the secretive companies of Israel that sells spyware to foreign governments. With no websites and few records available, it’s largely operated under the radar.
Candiru can infect androids, iPhones, Macs, PCs, etc.
According to media reports, there are more than 750 websites that are linked to Candiru spyware. Nearly 100 activists, journalists, and dissatisfied people from 10 countries have been targeted by Candiru’s spyware.
Who is Candiru?
Candiru is Tel Aviv, Israel, based furtive spyware company that provides undetectable spyware to foreign government customers. Their products are used to spy on computers, mobiles, iPhones, etc. Candiru makes its best efforts to keep its infrastructure, operations, and staff hidden from the public.

Candiru was found in 2014 and since then it has changed its name many times. The company’s current name is Saito Tech Ltd. but in the industry, it is still referred to as Candiru as they are most well-known by this name. candiru spyware was founded by Yaakov Weizmann and Eran Shorer, with the veteran chairperson Itzik Zack.
The logo of this company is in the shape of the letter “C” that represents Candiru fish.
| Company name | year |
| Candiru Ltd. | 2014 |
| DF Associates Ltd. | 2017 |
| Grindavik Solutions Ltd. | 2018 |
| Taveta Ltd. | 2019 |
| Saito Tech Ltd. | 2020 |
According to cybersecurity experts at the University of Toronto Citizen Lab, at least 100 activists, journalists, and political dissenters across 10 countries have been targeted that was made by Candiru. Candiru has developed almost 764 fake websites with domain names such as “Black Lives Matter”, “Amnesty Reports”, “Refugee International”, “Woman Studies”, “Euro Now”, and “CNN 24-7”.
Microsoft’s analysis also identified more than 100 victims around the world, including politicians, activists, and journalists as well as embassy staff from Israel, the Palestinian Authority, Iran, Lebanon, Yemen, Spain, Britain, Turkey, Armenia, and Singapore.
Dr. Bill Marczack, a senior researcher at the University of California at Berkeley told in a report that “they discovered several fake sites of human rights organization or activist organization”.
He further gave examples about these sites. For example, a site was named Amneystyreports.com was the fake website of Amnesty’s website. A site called Refugeeinternational.org was similar to the official website of Refugeesinternational.org, the difference was with just “s” in the middle.
There were many other fake websites of news (cnn24-7.online), technology companies(google play. store, apple-update. online, faceb00k-live. onlive and many more).
How does this Candiru spyware attack?
The tracking of illegal hacking is done by the Cyber Security Researcher of citizen lab. According to them, Candiru spyware takes advantage of the vulnerabilities in Windows. They further reported that Israel, Hungry, Indonesia, and elsewhere bought the spyware from Candiru and installed it remotely. Due to which many Windows were affected by taking advantage of the vulnerabilities.
What does Microsoft have to say about this?
As per the BlogSpot published by Microsoft on July 15th, 2021. Microsoft claims to have identified the websites that are tied to the spyware. Microsoft had disabled the cyberweapon of this spyware and has also created protection against it.
Candiru’s spyware made benefits by targeting the two exposures in Microsoft Windows Server, CVE 2021 33771 and CVE-2021-31979. Microsoft patched both vulnerabilities on July 13th,2021.
Microsoft has not referred to the company as Candiru. It referred to the spyware company as an “Israel-based private sector offensive actor”. Microsoft further said, “these companies increase the risk of weapons falling into wrong hands and endangering human rights”.
So, are Macs safe?
According to Tal Dilian, who claims to have a partnership with Candiru said: “even now Candiru specializes in hacking Windows, but it’s also working on tools to crack Apple’s macOS operating system”. He further said that he is not sure but candiru’s spyware may further be developed to attack iOS too.
Scott-Railton said that candiru was developing exploits for both Apple and Microsoft. He further added that “Tools like Candiru are used to expose fear”.
Who are the buyers of this harmful cyberweapon?
As per the reports Candiru had sales of nearly $30 million within two years of its founding. The Candiru firm’s clients are located in Europe, the Former Soviet Union, the Persian Gulf, Asia, and Latin America.
Candiru: Another Silent Weapon Discovered
A leaked candiru project details were published by TheMarker shows that the spyware can be installed in many different ways like through links and man middle attack, a vector named “sherlock” is said to work on Windows, iOS, and Android.
16 million euro – unlimited spyware infections, monitoring of 10 devices at a time
additional 1.5 million euro – monitoring of 15 devices at a time infect devices in 1 additional country
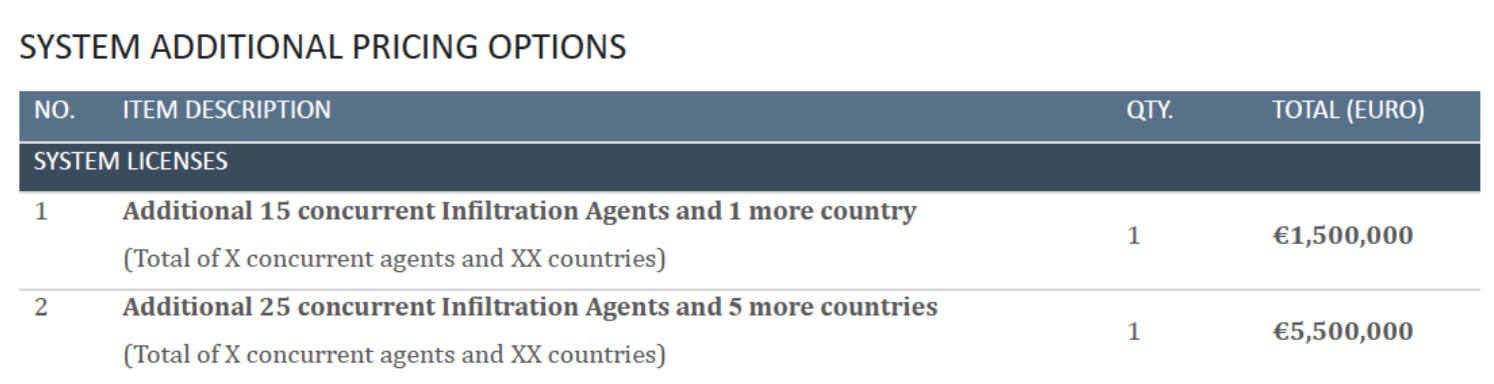
additional 5.5 million euro – monitoring of 25 devices at a time infect devices in 5 additional country

How Candiru’s spyware was exposed?
According to Forbes reports, Batholomew, a researcher at Russian Cybersecurity company Kaspersky Lab told them that how Uzbekistan’s mistake leads him and his team to expose Candiru’s spyware.
According to Bartholomew, Uzbekistan’s biggest mistake was to set up a test computer that was exposed on the internet. This computer was used to test its hacking tools against various antivirus systems including Kaspersky as well.
Bartholomew’s team found that computer online and noted that it was regularly connecting to a single Web address. This web address was not only registered in Uzbekistan but the registrant was the apparent leader of “Military Unit 02616”.
Though Bartholomew has little information about this he and his team soon discovered that it was part of Uzbekistan’s surveillance agency, the National Security Service (NSS).
Now, a very interesting part Barthelomow told is that the NSS has a history of buying malware from foreign dealers. They have also found e-mails that contain frequent messages about the deals between the hacking team and the unit. Bartholomew believes that Uzbekistan spent nearly $1 million for buying these cyberweapons.
Bartholomew further added that Candiru’s spyware exposure also led them to its two more customers that are Saudi Arabia and the U.A.E.
On this John Scott- Railton, a surveillance market researcher at the University of Toronto’s Citizen Lab says “each of these countries government is a serial spyware abuser, and it is painful to know that civil society got targeted again”.
Relation between Candiru and NSO (Pegasus)!
Now the question is what does John Scott- Railton meant by “AGAIN”. Here comes the relation between “Candiru” and “NSO”. Candiru is not the first but second company of Israel that has created such a cyberweapon. NSO Group is the first company which has created Pegasus.
According to the reports NSO made Pegasus was used to hack into the phones of politicians, human activists, journalists, lawyers, and including heads of state in the countries like UAE, Saudi Arabia, Morocco, Mexico, Hungry, India, and many others.
Pegasus was capable of reading text messages, collecting passwords, location tracking, and much other personal information including browser history.
Candiru’s spyware has similar features to NSO groups Pegasus. These Israeli firms have become rivals over the sales of spyware to the foreign government.
Candiru was working in hidden ways till now, but its rival NSO Group has been in many controversies. In Mexico, the use of NSO malware Pegasus lead to monitor journalists, activists, and lawyers working on the 2014 killing of 43 students caused a major political scandal.
According to a Forbes report, they attempted to contact Zack as well as the Candiru CEO Eitan Achlow, but could not receive any response from them. An NSO spokesperson said: “NSO is not connected to Candiru”.
How does candiru provide its services?
A leaked Candiru project proposal published by The Marker says that Candiru’s spyware can be installed using a different number of vectors, including malicious links, man-in-middle attacks, and physical attacks.
Candiru made spyware that has a number of targets that can be under active surveillance at anyone instant at any time. Like NSO Group, Candiru also restricts its customers to a set of approved countries.
Candiru’s spyware is a 16 million Euro project that allows an unlimited number of spyware infection attempts, but the monitoring will be allowed of only 10 devices at one time.
For additional 1.5 million euro is charged by Candiru, in this, the customer can purchase the ability to monitor 15 additional devices simultaneously, and to infect devices in a single additional country. For an additional 5.5 million euros, the customer can monitor 25 additional devices simultaneously, and conduct this cyberweapon in five more countries.
Candiru spyware also provides its customer remote shell capability for 1.5 million euros, which allows them full access to run any command or program on the target’s computer. This kind of activity is very concerning as the hacker can download any harmful file in the target’s computer system.
The reports state that the product will be operated in all agreed territories but it also has a list of restricted countries that include the US, Russia, China, Israel, and Iran. This same list was provided by the NSO Group for the use of Pegasus.
But according to Microsoft, it has been observed that Candiru does operate in restricted territories as well.
ARTICLE CREDIT TO: https://citizenlab.ca/